Making S3 Buckets Non-Public
Reason For Securing S3
Having a bucket be publicly exposed is not reccomended in S3. For the use case of putting everything behind Cloudfront to be hosted, it is probably fine.
But I wanted to get a better understanding of roles in S3, so I decided to try. Now that I had a bit more familiarity with roles.
I wanted to include a picture, but I couldn’t find a way to get the bucket to be public. Easily. Which is good, AWS fixed that in the last year or so.
Creating the role in S3
The permissions are configured at the bucket level in S3 using JSON.
The structure of the role will be similar to the below, but you’ll have to replace your-bucket-name and EXAMPLEJJIO3T0
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Cloud Front Read Object",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::cloudfront:user/CloudFront Origin Access Identity EXAMPLEJJIO3T0"
},
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::your-bucket-name/*"
}
]
}
Create a CloudFront Origin Access Identity
I could only find a way to do this when creating a Distribution, or when adding a new origin to a distribution. I wasn’t able to find a way to use an OAI with an existing origin.
- Go to CloudFront
- Click Create distribution
- Create OAI
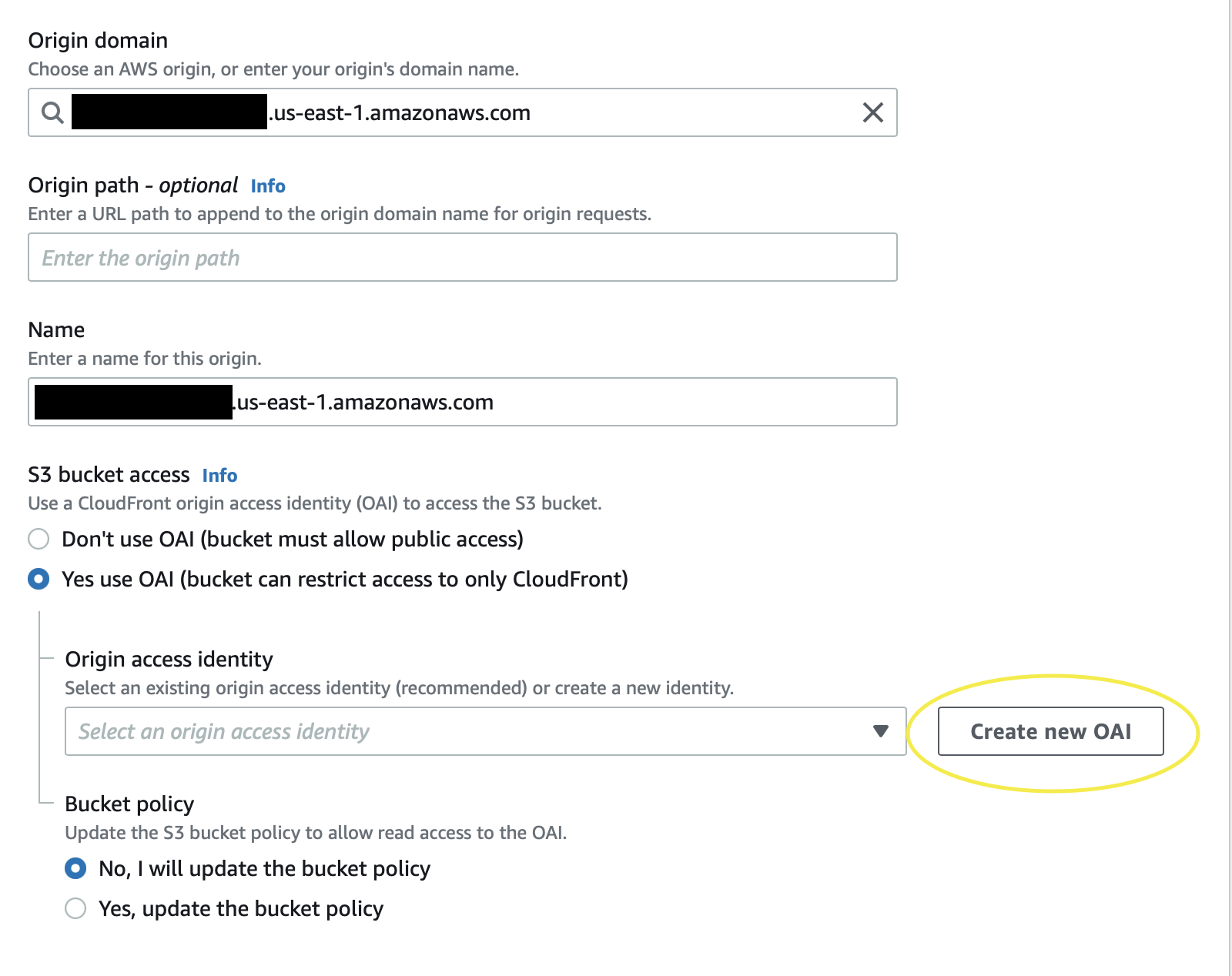
- Select
Yes use OAI - Click
Create new OAI
- Select
Modyify the S3 Permissions to use the OAI you created
- Go to S3
- Click on the bucket you want to allow the distribution to have access to
- Click on Permissions
- Paste the template into the editor.
- Replace
your-bucket-namewith the bucket you want to use - Replace EXAMPLEJJIO3T0 with the ID of the OAI you created
- Click Save